#Cybersécurité
#Cybersecurity
#Digital

03/11/2022
Incident Management, although an essential strategy for any business, is not yet defined everywhere. However, in a year marked by cyberattacks, companies should no longer hesitate to implement it quickly!
So, how can incident management be established, what roles need to be defined, and for whom? Luc Cottin and Matthieu Jungers, CEO and ISO at Rsecure, along with Serge Sauvage, Director of Compliance at Rcube, explain it all!
Today, there are three types of individuals affected by cyberattacks: customers, suppliers, and hackers. Cybersecurity specialized companies certainly have their hands full!
These hackers, or shall we say attackers, can engage directly in criminal activities or carry out espionage, cyber activism, terrorism, or even warfare. To effectively respond to these situations, companies need to prepare themselves adequately!
Several scenarios are possible and will enable you to effectively combat attacks, regardless of their nature. Among these solutions are BCP (Business Continuity Plan), DRP (Disaster Recovery Plan), and CRP (Cyber-resilience Plan).
The Business Continuity Plan (BCP) is a contingency plan implemented when a company’s premises become unusable for employees. Thus, if a disaster were to occur within your building, your BCP would automatically kick in and allow you to work elsewhere safely. The Cyber-resilience Plan (CRP), on the other hand, ensures data recovery despite a cyber event. Finally, the Disaster Recovery Plan is the process of maintaining or restoring infrastructure after a disaster.
For each of the mentioned scenarios, clear and defined plans based on the strategy to be implemented will be proposed, taking into account the nature of the disaster and its priorities. However, when defining the various strategies, it is essential to consider the business areas affected by the disaster and the top priorities.
In general, our work methodology to address cyber risks is based on a strategy recently developed by Rsecure, the H.O.P methodology. Focused on three levels – Humans, Tools, and Processes, this methodology measures a company’s cyber maturity and guides the adoption of necessary support and measures. Regarding humans, the goal is to analyze risks and train teams to detect existing threats and respond effectively. Tools allow for the measurement and detection of system vulnerabilities within the company, as well as long-term protection. Processes, on the other hand, ensure compliance with standards and policies that regulate the behaviors of employees and the company.
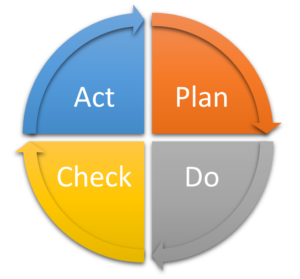
In parallel with this strategy, the Deming Wheel helps prepare for the best possible action. It is divided into four stages that help employees in a company define a comprehensive and clear action plan for everyone: Plan, Do, Check, Act.
Let’s focus first on the Business Impact Analysis of incident management. This BIA will serve as a basis for linking the business with all existing risks to identify potential sources of incidents. You will be able to define financial and legal impact levels based on your services and systems in place. From this, user training procedures will emerge to help them prepare for the best possible action.
Once these procedures are created, they should be implemented and tested because they form the basis of your ability to respond concretely to an incident. This capability improves from one incident to another, as the company reviews what worked and what didn’t.
There are Business Impact Analysis (BIA) models, mainly governed by various regulator circulars, which provide reading grids and require regulated companies to adhere to certain basic evaluation parameters (financial, legal, etc.).
The BIA will also help identify the priorities of the incidents analyzed based on pre-established criteria such as the number of affected devices, the type of incident in progress, etc. These priorities will be categorized by importance level, from level 1 minor to level 4 major. For each of these incidents, it is necessary to define the roles of the responsible individuals. If it is an IT incident, the IT support and IT committee will be at the forefront. If it is more of a cyberattack, the Security Officers and the CISO will take charge of the situation. And finally, if it is a natural disaster, it is up to the Business Continuity Plan manager or the Local Facility manager to handle the incident.
When the company faces a major incident, the designated responsible individuals must communicate with the emergency team, including the BCP Manager, CISO, CTO, etc. To do this, they should use a communication tool that sends SMS messages to the members of this team to identify the nature of the event, its impact on the company, and the decisions to be made to address it. Please note that the communication tools used during the resolution process should be external to the company to avoid complications during the incident.
If the impact is too high for the contacted committee, the Crisis Management Team (CMT) should step in using the same communication tool between each of the following steps. And once again, if the situation does not improve, it is necessary to expand the scope of responsibilities and involve the “board.” Do not involve people solely to expand the team! Each member must be aware of their responsibility in the decisions made and implemented.
Regarding tools, there are several options (alert systems, SaaS solutions, etc.). Always ensure that they are external to the company to prevent them from being impacted by the incident.
Now you know how to organize your Incident Management to better cope with cyberattacks or disasters in your company!
More info about incident management ?
Revew the webinar (FR)